Introduction
The Hivestorm competition is a blue-team defense-style competition where each team is given 5 vulnerable virtual machines of varying operating systems. The goal of the competition is to patch as many vulnerabilities as possible. This writeup won’t be going into too much detail on how to audit or how to prepare for the competition. It will, instead, go over many checks from each virtual machine and how to fix them. My team ran into a few issues which you will read about below, but we had a very good and in-depth retrospective where we went over what we missed and identified other checks that we missed out on. None of this would have been possible without my team, so I would like to thank them for their hard work and dedication to the competition.
Frustrations
My team and I practiced very intensively for this competition and did all of the practice required for it. We spent a lot of time writing scripts (Which you can now find on my Github) and preparing for the day of competition. My frustrations stem from issues with the competition VMs which I believe resulted in us ending up only third place. The practice virtual machines that were distributed were the same as the ones from the prior year, and they ran with no issues on our machines. The competition VMs, however, refused to work on our laptops. The support team had no idea what was wrong and we ended up losing two full hours of competition time on the Windows virtual machines due to these issues. We had to spend time slowly downloading the Windows Server virtual machines from the (stressed) competition server on a second desktop we fortunately had. This was a huge waste of time and I believe it cost us the competition.
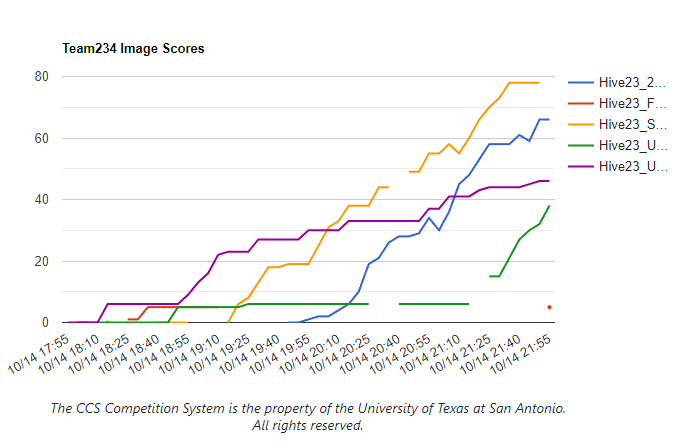
The issue ended up stemming from the version of VMWare Tools the Hivestorm team distributed with the virtual machines. The version of VMWare Tools was incompatible with the version of VMWare Workstation we were using. This resulted in the virtual machines not being able to boot properly or not being able to display anything. We could not back out since our time had already started on the Unix virtual machine. You can find many people referencing boot issues in the Hivestorm Discord. I believe this is a huge oversight on the Hivestorm team’s part and I hope they fix it for next year. I do believe I would have been able to squeeze out 1 more point (Which we were beaten by) if we had that time back. You can see our image score graph below.
Overview
This writeup will be split into two major sections: Windows & Unix machines. I will go over each box in detail and explain how each vulnerability was patched.
Windows
Windows Server 1
The first (and second) of the Windows virtual machines were running Windows Server 2019.The Readme for the virtual machine specified a few key details, especially about how the machine was hosting an IIS web server. The Readme also includes a list of authorized users and administrators.
Checks
I will split the checks into a few different policies, such as users and policies. First, however, we need to go over the forensics questions.
Forensics
The forensics questions are high value questions which require a dive into the machine and require utilization of system tools to find the answer(s).
The first forensics question is as follows:
After gaining access to this machine, an attacker proceeded to install a
malicious program using a batch (.bat) script. Afterwards, the attacker deleted
the script from the machine.
What is the absolute path that the script was located at before being deleted?
( EXAMPLE: C:\Windows\System32\Build.bat )
ANSWER:
What is the file size in bytes of the script?
( EXAMPLE: 15871 )
ANSWER:
What is the timestamp of when the malicious script was deleted in UTC?
Please provide the timestamp in the MM/DD/YYYY HH:MM:SS format.
( EXAMPLE: 10/21/2004 05:11:14 )
ANSWER:
Since it is the first forensics question, it’s quite easy. To find the deleted batch file you can just open the Recycle Bin and find the file. You can restore it then follow it to get the proper sequence of answers:
ANSWER: C:\Users\eshane\Desktop\install.bat
ANSWER: 1772
ANSWER: 09/20/2023 23:45:08
The second forensics question asks the following:
This machine is currently used to host a scoreboard for a competition between
a few slingers. You can visit http://localhost/ to view the current scoreboard.
The web admin also set up a page to update a players score using a password.
The password appears to be set to "240610708" without quotes, however there is
an extra check to ensure this password cannot be used.
What is the MD5 hash of a valid password to update a team on the scoreboard?
( EXAMPLE: cc3a0280e4fc1415930899896574e118 )
ANSWER:
I’m not entirely sure how this one was meant to be solved. I just ran md5sum on the word password for the lolz, input the hash as the answer, and got points for it, but I have a feeling that isn’t right.
The third and final forensics question is as follows:
There is currently a malicious program running as a Windows service that
persistantly reinstalls and restarts the GooseDesktop software. This service
also reinstalls itself and tries to maintain its own persistance. However, if a
specific "killswitch" file exists, the program will exit on startup.
What is the absolute path to the "killswitch" file?
( EXAMPLE: C:\Windows\backdoor.csv )
ANSWER: Type Answer Here
This one is pretty easy to find so long as you can check what files the malcious service is trying to open, you can quickly find out that there is a failed file read attempt on
C:\Windows\Temp\goosekill.txt. Creating this file uninstalled the Goose executable verifying that this is the answer.
Users
On this machine, there were 6 total scored items related to users. On Windows these are very easy points and should be done first.
I don’t think there’s much need to go into detail on all of these checks so I will just list them off in bullet-point style. Keep in mind that you need to use the Server Manager/AD User page to change/fixed these issues.
All Checks:
- Default
Administratoraccount needs to be deleted - User
junjieshould not be an administrator - User
dbaneshould not exist, delete it - User
twistshould not exist, delete it - User
pingwas disabled, enable it - User
tadshould not exist, delete it
These checks net you between 1-2 points each, so it is worth getting, but not worth wasting a lot of time on.
Policies
Policies are anything related to both the registry and settings within the Server Manager. These are also very easy points so long as you know what to look for.
You have 4 hours, so you should be spending a lot of time going through each of the policies and double checking that they are all set correctly according to a known benchmark.
Password/Account Policy
The password policy is free points and they’re typically all located in the same spot in the Local Security Policy. Account policies are very similar, which is why I group these together.
Account Policy Checks:
- Max Password Age is not set properly
- Ensure Lockout Threshold and Lockout Observation Window are set properly
- You can find a good resource for this here: https://theitbros.com/change-account-lockout-policy/
Surprisingly, there weren’t that many checks for password policy this year compared to last, but that’s okay, we have other policies to check.
Audit Policy
The audit policy checks are once again very quick to do an to check. They are located in the local security policy and it’s pretty simple to go through and set them up to audit for failure or success depending on the benchmark you check.
For this virtual machine there were only two audit policies that needed to be checked:
- Audit Computer Account Management
- Set to
Success
- Set to
- Audit Other Account Management
- Set to
Failure
- Set to
This is kind of trial-and-error, testing what does work and what doesn’t for the checks.
System Policy
Pretty self-explanatory, these are settings which define how the system behaves in different scenarios. Most of these settings can be set in the Local Group Policy Editor. These checks were worth a decent chunk of points while also being pretty easy to audit.
List of System Policy Checks:
- Shutdown: Allow system to be shut down without having to log on
- Set to
Disabled(0)
- Set to
- User Account Control: Allow UIAccess applications to prompt for elevation without using the secure desktop
- Set to
Disabled(0)
- Set to
- Interactive logon: Do not display last user name
- Set to
Enabled(1)
- Set to
- User Rights Assignment: Create global objects
- Set to
AdministratorsandLocal Service
- Set to
- User Rights Assignment: Modify firmware environment values
- Set to
Administrators
- Set to
- Early Launch Antimalware: Boot-Start Driver Initialization Policy
- Set to
All(7)
- Set to
Services
The critical/required services were outlined earlier in the Readme, so we should usually start there to ensure they are configured properly. Googling common audits for these services will usually yield the correct answer. I will briefly go over the checks that were employed for the active services, or services that should not be running.
Service Checks:
IIS‘WebServer’ is a file share, and it should not be.- Can be disabled via System Tools -> Shared Folders -> Shares
MySQLservice should not exist or be running.- Can be disabled via
services.msc
- Can be disabled via
SEMgrSvcshould be not be running (Not a critical service).- Can be disabled via
services.msc. Set start type toDisabled
- Can be disabled via
These are all easily auditable via services.msc or any other service viewer. Next I will cover service specific policies which may be a bit more difficult to audit.
RDP
The following checks can be configured in gpedit.msc under Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host
- Allow users to connect remotely using Remote Desktop Services ( Located in Connections tab)
- Set to ‘Enabled’
- Require secure RPC communication ( Located in Security tab )
- Set to ‘Enabled’ (1)
IIS
There’s not much to say about the IIS service since it’s clearly marked as required. All I had to do was google a quick benchmark and I was able to find where to configure and audit the settings.
All of these checks can be done in IIS Manager.
IIS Checks:
- Ensure Identity Type is set to
ApplicationPoolIdentity- Located in
IIS Manager -> Application Pools -> DefaultAppPool -> Advanced Settings -> Identity
- Located in
PHP
PHP is a required service since the web server is running it.
Nearly all of your auditing should be spent in the php.ini file. This file was located at C:\Program Files\PHP\v5.6\php.ini.
The checks for PHP are as follows:
- Ensure
disabled_functionsis set toexec,passthru,shell_exec,proc_open,popen,curl_exec,curl_multi_exec,parse_ini_file,show_source,system- Not sure which one of these did it, but one of them did.
- Ensure
display_errorsis set toOff- Set to
Off(0)
- Set to
Malware & Unwanted Software
This section is pretty self-explanatory. You need to find and remove any malware or unwanted software on the machine. This is usually done by checking the Program Files directory and looking for anything that looks out of place.
One of the common places Hivestorm hides Malware is in the C:\Windows directory. I wrote a quick powershell script to iterate through it and check for anything which isn’t signed by Microsoft Corp.
Software and Malware:
- John is installed in C:\ProgramData\Microsoft\John
- Delete the directory or executable
- Remove SetHC from registry keys
- HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe
- Goose is installed in 5 places
- C:\Program Files\GooseDesktop
- C:\Program Files (x86)\GooseDesktop
- C:\ProgramData\GooseDesktop
- C:\Users\Public\Documents\GooseDesktop
- C:\Users\eshane\Downloads\GooseDesktop
- All of these can be deleted
- Remove Fake DllHost from C:\Windows\System32
- Named ‘dIIhost.exe’
Windows Server 2
Very similar to the first Windows Server in terms of overall procedure and steps. The biggest difference you will find with this box is the critical services and ‘purpose’ of the virtual machine for the competition scenario. This server was described as a Domain Controller, DNS server, and a certificate server. All of this is VERY important to know as it points us in a direction to audit.
Forensics
Question 1
The forensics questions on this machine were admittedly a bit more difficult than the first machine. The first question was as follows:
On your desktop there is a partial physical image of a damaged camera's memory
card labeled, "Partial-Camera-Memory-Card-Recovered.vhd". As a result of the
damage, we have been unable to recover the files but the majority of the file
system's core files are still intact. There is an allocated file within this
file system with the word "House" within the file name that we would like some
additional information on.
What is the full file name and the cluster chain of this file?
HINT: To learn more about clusters, cluster chains, and the FAT filesystem, see
https://en.wikipedia.org/wiki/Design_of_the_FAT_file_system
NOTE: Make sure to follow the cluster chain format in the example below.
Cluster numbers should be specified in decimal (base 10) and separated by a
single - (dash).
( EXAMPLE: In-The-House-23.jpg )
( EXAMPLE: 123-124-125-126-234-235-236-237 )
ANSWER:
ANSWER:
The server, thankfully, includes a folder on the Desktop which has a plethora of ‘Authorized’ tools, including Autopsy my beloved.
Using Autopsy makes this insanely trivial to solve so long as you can get around the ‘damaged’ part of the memory card.
Because I do not know everything, I found this article pretty useful for explaining some parts of the filesystem: https://www.ntfs.com/assemble-clusters.htm
Autopsy reveals a file named White-House-22.png
Tracking our own cluster chain and formatting our answer like the example yields the following: 183-184-185-186-187-188-189-190-191-192
Question 2
The second Forensics question is admittedly a bit easier than the first as it doesn’t require you to install any special software or tools. The question is as follows:
Network security detected an unauthorized RDP session coming from this
computer.
What is the full URL of the website being viewed in the unauthorized RDP
session?
( EXAMPLE: https://www.hivestorm.org/competitions/current-competition/competition-schedule )
ANSWER:
I had no idea how to do this originally since I’ve never tried. Thankfully google knows the answer! I found this very useful post which gave me a LOT of options: https://serverfault.com/questions/758930/how-can-i-view-active-remote-connections-rdp-to-a-windows-server
Using this article we can see that there is an RDP session coming from the user ARivera. By viewing the session, we can see they are currently viewing the website https://www.zerodayinitiative.com/advisories/ZDI-22-1690/
And that’s pretty much it for forensics question 2. I found it a little odd that question 2 was easier than question 1, as usually they increase in difficulty.
Question 3
The third and final forensics question, which was easily the most time consuming, was as follows:
The marketing department was recently hit with a ransomware attack.
Our emergency response team recovered an object file, encrypt.obj from the
malware. The encrypt.obj file is located on your desktop. This malware uses
a simple xor encryption scheme.
RBaxter has asked you to decrypt an important file on your desktop named
"encrypted". Unfortunately RBaxter did not have a backup of this file.
After decrypting the file named "encrypted", what is the MD5 sum (hash) of the
original (unencrypted) file?
( EXAMPLE: 5541F598FE0AF1594862461B6BCAC3F5 )
ANSWER:
TODO: Find the python script
Users
This machine requires a bit more in-depth audit of all users in order to maximize your points, but it’s still pretty easy to do. I will list off all of the checks and how to fix them. All of these checks should be done under the Active Directory Users and Computers tool.
Remember to consult the Readme to see who should be on the computer and who shouldn’t be.
User Checks:
- System
Guestaccount should be disabled- Delete the user by right clicking and selecting
Delete
- Delete the user by right clicking and selecting
- User
SSamuelshas his password (October@2022) in his ‘Notes’ section- Remove the password from the notes section
- Also reset his password as it is insecure
- User
Stanleyis currently locked out- Unlock the user by entering properties and ticking the
Unlock accountbox and clickingApply
- Unlock the user by entering properties and ticking the
- User
Tashinais in the Administrators group- Remove the user from the Administrators group in the properties
- User
SMartinezhas no active logon hours set, whereas every other user does- Set the logon hours to match the other users
- User
ARiverais not an authorized user- Delete the user by right clicking and selecting
Delete
- Delete the user by right clicking and selecting
Policies
Similar to Windows Server 1, you can find nearly all of these incorrect policies by going through the Local Security Policy and the Group Policy Editor. I will list off all of the checks we found and how they should be fixed.
Policy Checks:
- Credential UI should not enumerate administrator accounts on elevation
- This can be found in the Local Security Policy under
Administrative Templates -> Windows Components -> Credential User Interface - Set to
Disabled
- This can be found in the Local Security Policy under
- Password Maximum Password Age is not set properly
- This can be found in the Local Security Policy under
Account Policies -> Password Policy - Set to
90days
- This can be found in the Local Security Policy under
- Allow Log on Locally is not set properly
- This can be found in the Local Security Policy under
Local Policies -> User Rights Assignment - Set to
Administrators - Good resource: https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/allow-log-on-locally
- This can be found in the Local Security Policy under
- Computer Account Management audit policy is not set properly
- This can be found in the Local Security Policy under
Advanced Audit Policy Configuration -> System Audit Policies - Local Group Policy Object -> Account Management - Set to
Failure
- This can be found in the Local Security Policy under
Services
There are a couple things to consider regarding services: Status and options.
Status refers to whether a service should or should not be running, and options refers to the security/hardening options for a service that is meant to be running.
Nearly all status checks can be configured in services.msc or Server Manager. The options checks can be configured in gpedit.msc or Server Manager.
Service Status Checks:
- Windows Update Service is not running
- Ensure it’s enabled and set to
Automatic
- Ensure it’s enabled and set to
- Printer Spooler service is not critical and is running
- Stop the service and set it to
Disabled
- Stop the service and set it to
- Windows Remote Management service is running
- Stop the service and set it to
Disabled
- Stop the service and set it to
Service Options:
- DNS Multicast name resolution is not properly configured
- Located in
Administrative Templates -> DNS Client - Option:
Turn off multicast name resolution - Set to
Enabled(0)
- Located in
- DNS Zone Transfers are not allowed or set to whitelisted servers
- Can be found in
wh.localproperties underZone Transfers - Set to
Only to servers listed on the Name Servers tab
- Can be found in
- DNS Cache is not secured against pollution
- Can be found in
wh.localproperties underAdvanced - Set
Secure cache against pollutiontoEnabled
- Can be found in
- DNS Event Logging is disabled
- Can be audited using Powershell command
Get-DnsServerDiagnostics - Set via:
Set-DnsServerDiagnostics -EventLogLevel 2 - Resource: https://learn.microsoft.com/en-us/powershell/module/dnsserver/set-dnsserverdiagnostics?view=windowsserver2022-ps
- Can be audited using Powershell command
- MS Network Client is not digitally signing communications
- Located in
Local Policies -> Security Options - Option:
Microsoft network client: Digitally sign communications (always) - Set to
Enabled
- Located in
- Encryption Types are not properly configured for Kerberos
- Located in
Local Policies -> Security Options - Option:
Network security: Configure encryption types allowed for Kerberos - Set to
AES128_HMAC_SHA1, AES256_HMAC_SHA1, Future encryption types
- Located in
- LDAP Server signing is not set to
Require signing- Located in
Local Policies -> Security Options - Option:
Domain controller: LDAP server signing requirements - Set to
Require signing
- Located in
- Print Service is allowing all users to add printer drivers
- Located in
Local Policies -> Security Options - Option:
Devices: Prevent users from installing printer drivers - Set to
Enabled
- Located in
- CA Service need auditing enabled
- Can be set via
certsrv.mscunderCA -> Properties -> Auditing - Audit
start/stopandIssue and manage certificate requests - Can be set in
Object AccessunderAdvanced Audit Policy Configuration -> Audit Policies - Resource: https://www.pkisolutions.com/enabling-active-directory-certificate-services-adcs-advanced-audit/
- Can be set via
- CA Service group security permissions are misconfigured
- Fix under
CA -> Properties -> Security - Ensure all groups have the proper permissions
- Fix under
Malware and Software
As the Readme says, there are a few programs that need to be updated to the latest version. This points us in the right direction to start. The procedure is the same as the first Windows Server, so I need to check the task manager, check installed programs, and then search for malware.
Software Specific Checks:
- FireFox needs to be updated
- Update the program to the latest version
- FireFox needs HTTPS only mode enabled
- Setting located in the
Privacy & Securitytab - Enable HTTPS only mode in the settings
- Set to
all windows
- Setting located in the
- Internet Explorer is not secure
- Need to enable IE hardening
- This can be enabled in the
Server Managerdashboard - Can also be enabled via
gpedit.mscunderComputer Configuration -> Administrative Templates -> Windows Components -> Internet Explorer
- WSL is enabled
- Disable WSL via
Turn Windows Features On or Off
- Disable WSL via
- Audacity is installed
- Uninstall Audacity
- TVNServer is installed
- Uninstall TVNServer
Regarding Malware, I’m sure I missed one or two, but I am unsure where they are or how to locate them. I used the same Powershell script from the previous box to search for any Malware in the C:\Windows directory, but I am unsure still, even post-competition during our retrospect.
Malware Specific Checks:
- Unknown ISO located in hidden Windows folder
- Located at
C:\ProgramData\Microsoft\Windows Security Health\recovery.iso - Must be removed
- Located at
- Netcat backdoor running in Debian WSL container
- Can be found by fully deleting the Debian WSL container
Misc. Checks
Not sure where else to put these, but there are some checks which I don’t think fit into any other categories.
Misc. Checks:
default.rdpfile inside unauthorized user’s Documents directory- Located at
C:\Users\ARivera\Documents\default.rdp - Hidden files need to be enabled in File Explorer to see this one
- Located at
- HKLM\SYSTEM has incorrect permissions
- Everyone has access to write to this
- Fix by setting permissions to
AdministratorsandSYSTEM
Windows Conclusion
I’m sure I missed a few things, but I think I got most of it. I will update this section if I find anything else. I may have also forgotten some of the checks that we ended up getting.
Unix
While Windows and Unix are completely different operating systems, the general procedure for these images was near identical. It should be noted that our usage of the desktop GUIs that were pre-installed on the VMs was quite limited and we instead relied on scripts we wrote and the bash command line.
There were three Unix based virtual machines in total: Ubuntu 1, Ubuntu 2, and Fedora. We got the most work done on Ubuntu 1 and 2 during the competition and retrospective. Our work on Fedora was quite limited due to time constraints. If you are more interested in these time constraints please refer to this section.
If you are interested in our scripts for Unix systems, you can find them on my Github here: https://github.com/SystematicSkid/py-storm
For the Ubuntu machines I will go over the forensics then go through a list of checks similar to the Windows machines.
Ubuntu 1
The provided readme defines some keys points for the virtual machine such as: All packages needing to be updated, FireFox should be updated, LibreOffice must be updated, and UFW needs to be enabled.
Some critical services are also defined:
- Apache Web Server
- MySQL/MariaDB
- PHP-FPM
- OpenSSH Server
Forensics
Question 1
The first question starts off pretty simple, requiring us to use just a few commands:
There is a ruby backdoor on this system that changes its own process title and
arguments after executing, which is displayed by various system tools.
What is the process title of the ruby backdoor as displayed by standard system
tools?
( EXAMPLE: avahi-daemon )
ANSWER:
This backdoor can be found very easily by examining running processes and looking for anything using ruby.
With a little bit of searching you can identify a process with the title of [scci-loop] which is the answer to the question.
Question 2
The second and final forensics question for this machine is directly related to the previous one:
There is a ruby backdoor on this system that requires a password to access it.
What is the password needed in order to access this machine through the
backdoor?
( EXAMPLE: password123 )
ANSWER:
Since the process should have already been found, it is quite easy to employ a more in-depth investigation to discover the password for the backdoor.
The password used for the backdoor is knock-knock.
User Checks
Thankfully, we wrote over a few hundred lines worth of scripts for users and groups specifically, so it was fairly easy to narrow down the checks for this machine. Just like Windows, these checks are not worth an insane amount of points, so not much time should be spent on them if you can’t spot them right away.
Similar to Windows, refer to the readme constantly to who should be on the system and their proper role.
User Checks:
- User
dnachoexists on the system- Delete the user
- User
tblakkexists on the system- Delete the user
- User
emperorexists on the system- Delete the user
- User
grendelis set to automatically log in- This can be audited in the
/etc/pam.d/*files - Remove
grendelfrompam_succeed_if.soin the file
- This can be audited in the
- User
binhas a login- Remove this user’s login by setting the shell to
/sbin/nologin - Can also be fixed by setting the password field to
*in/etc/shadow
- Remove this user’s login by setting the shell to
- Suder group
scoringshouldn’t exist- Delete this group
- Located in
/etc/sudoers.d/
- User
mmilfordhas no maximum password age- This is defined in
/etc/shadow - Set the password age to
90days- The password age field is the fourth field in the file
- This is defined in
- User
docis a sudoer, but he should not be- This can be audited in the
/etc/groupfile
- This can be audited in the
System
The system checks include things like the firewall and anti-virus related checks and some miscellaneous ones that didn’t fit in other categories. Most of these checks are pretty simple and easy to do, but some of them require a bit more in-depth knowledge of the system.
System Checks:
- Firewall is not enabled
- Enable the firewall via
sudo ufw enable - Can also be enabled via
/etc/ufw/ufw.conf
- Enable the firewall via
- Grub does not have DEP enabled
- Can be found in
/boot/grub/grub.cfg - Set
noexectoonin thelinuxline
- Can be found in
tmpfsis not mounted withnoexec- Can be found in
/etc/fstab - Set
noexecon thetmpfsmount
- Can be found in
LLMNRis enabled- Can be found in
/etc/systemd/resolved.conf - Set
LLMNRtono
- Can be found in
Policies
Policies on Unix systems are defined a bit differently (for us anyways) from how they are defined on Windows systems. Our scripts do extensive checks on password policies, ssh policies, and some others. I will not go over our scripts, but I will go over the ‘policy’ checks that were deployed on this machine.
Policy Checks:
- Default sudoer policy is set to not require a password
- Can be found in
/etc/sudoers - Insecure option, ensure users have to input password to sudo
- Remove
!authenticatefrom the file
- Can be found in
- GDM3 is not rejecting TCP
- Can be set in
/etc/gdm3/custom.conf - Set
DisallowTCPtotrue
- Can be set in
- Security
pwqaulitymodule does not havegecoscheckenabled- Ensure
pam_pwqualityis loaded by checking/etc/pam.d/common-password - Ensure
pam_unixis loaded by checking/etc/pam.d/common-password - Ensure
gecoscheckis not set to 0 in/etc/security/pwquality.conf
- Ensure
- TCP Synack retries are misconfigured
- Configured in
/etc/sysctl.conf - Set
net.ipv4.tcp_synack_retriesto2
- Configured in
- Kernel pointers are not restricted through
/proc- Configured in
/etc/sysctl.conf - Set
kernel.kptr_restrictto2
- Configured in
Services
As noted in the introduction to this virtual machine, there are several critical services that need to be operational, updated, and secure. Most of these are fairly easy to update and don’t take much time at all. Some of the more security-related options can take some research to get though.
Service Checks:
nginxneeds to be updated- Update via
sudo apt update && sudo apt upgrade
- Update via
- nginx has server tokens enabled
- Configured in
/etc/nginx/nginx.conf - Set
server_tokenstooff
- Configured in
- nginx does not have XSS protection enabled
- Configured in
/etc/nginx/nginx.conf - Set
X-XSS-Protectionto1; mode=block
- Configured in
mysqld/mariadbneeds to be updated- Update via
sudo apt update && sudo apt upgrade
- Update via
- mysql does not have
bind_addressproperly configured- Configured in
/etc/mysql/my.cnf - Set
bind_addresstolocalhost
- Configured in
libreofficeneeds to be updated- Update via
sudo apt update && sudo apt upgrade
- Update via
- SSH has PermitRootLogin enabled
- Configured in
/etc/ssh/sshd_config - Set
PermitRootLogintono
- Configured in
Unauthorized Software & Malware
There’s a lot of unauthorized data and files on this system which really just equates to easy points for the team. Identifying what shouldn’t be there may be hard though. Thankfully this writeup will show you most of what to look for.
Software and Malware:
- Unauthorized mp3 file in
/usr/share- Delete
slugterra_shot_sound.mp3
- Delete
- Possible malicious backup file located in phpbb
- Located in
/var/www/html/phpbb/assets/which is public facing - Delete
backup.html
- Located in
- Pentesting tool DNSniff is installed
- Remove from
/usr/bin/dnsniff
- Remove from
- UNO is installed via snap
- Remove via
sudo snap remove uno-java
- Remove via
- aircrack is installed on the system
- Remove via
sudo apt remove aircrack-ng
- Remove via
- Ruby backdoor
jnfis running- Kill the process running
usr/bin/ruby - Delete the backdoor in
/etc/systemd/system/multi-user.target.wants/jnf.service
- Kill the process running
- Remove the
socatmalware- Hidden in
/usr/bin/sqldbprocess- Kill this process
- Remove the cron job for
sqldb- Located in
/etc/cron.d/sqldb
- Located in
- Hidden in
Ubuntu 2
Ubuntu 1 and Ubuntu 2 are very different, besides sharing the same operating system. I don’t think they shared a single check between them, which is good for variety, but bad for time management. The only similar service defined in the readme was is the OpenSSH server.
Besides that, there are a few new critical services:
- Postfix (SMTP)
- Dovecot (IMAP)
- NFS Kernel Server (NFS)
- OpenSSH Server (SSH)
The readme also outlines some VM specific instructions that should net a good amount of points so long as they are followed properly and done as instructed.
Forensics
Question 1
The first forensics question is as follows:
There are two duplicate regular files in the /usr/ directory with a SHA256 sum
(hash) of deb1353bea87a41c4d5c012e898cc8b0e4af0f55e8dd4eaffe94ba66e9e34247.
What are the file names of the two files?
( EXAMPLE: copyright )
( EXAMPLE: debconf-communicate.1.gz )
ANSWER:
ANSWER:
This forensics question is a very simple bash test. These two files can be found using a combination of find, sha256sum, and grep like so:
find /usr/ -type f -exec sha256sum {} + | grep 'deb1353bea87a41c4d5c012e898cc8b0e4af0f55e8dd4eaffe94ba66e9e34247'
The output of this command is as follows:
d7c4d1e436877fd24c88a670819357035b1307.debug
network-online.png
Question 2
The second forensics question requires the user to extract a ‘hidden’ message from the secret file on the user’s desktop:
Major monogram has hidden a TOP SECRET message for you in the file on your
desktop named secret.
What is the secret message that Major Monogram has hidden?
NOTE: The secret message is not TOP SECRET
( EXAMPLE: TOP SECRET )
ANSWER:
As a CTF player, this is a fairly easy question, but I will leave you with this:
The best possible answer I can give
Question 3
The third and final forensics question is as follows:
Major monogram has a TOP SECRET project for you to work on.
Libraries, are loaded (or mapped) into the address space of a process when it
executes. For example, if you run "cat /proc/self/maps" you should see
something like:
55555554000-555555556000 r--p 00000000 08:02 1044644 /usr/bin/cat
555555556000-55555555a000 r-xp 00002000 08:02 1044644 /usr/bin/cat
Assume libc.so.6 will be loaded into memory at the address 7ffff7dd3000 when a
TOP SECRET program is being executed. You have no other knowledge of this TOP
SECRET program. A copy of libc.so.6 has been placed on your desktop.
Major monogram has asked you to find 3 things:
A) At what address in memory will the libc "system" function be located at?
B) At what address in memory will the string "/bin/sh" be located at?
C) At what address in memory is the FIRST occurrence of the bytes representing
the assembly instructions "pop rdi; ret"
NOTE: Make sure the addresses are in hex (base 16)
( EXAMPLE: 7FFFF7EA7980 )
( EXAMPLE: 7FFFF7F6AABE )
( EXAMPLE: 7FFFF7DFBED9 )
ANSWER:
ANSWER:
ANSWER:
As a professional pwn CTF player, this one is once again a very trivial and simple question to answer. This question pertains to ROP-chaining which a common technique used in binary exploitation. All of these answers can be found using pwntools python package.
Final answer:
ANSWER: 0x7FFFF7F69031
ANSWER: 0x7FFFF7DFA725
ANSWER: 0x7FFFF7E1F330
Users & Groups
These checks are identical in nature to the ones on Ubuntu 1, there are just less (afaik) and do require a bit more work.
User Checks:
- User
nfsshould not exist- Delete the user
- User
pinkyhas an insecure password- Reset the password to something secure
remotegroup is not properly configured- Configure in
/etc/group - The users
pinky,wanda,baljeet, andvanessaneed to be in theremotegroup
- Configure in
- SSH keys must be configured exactly as the readme describes with RSA and
PubKeyAuthenticationset toyes
System Checks
Some of these checks are identical to the first Ubuntu box, but there are still quite a few different misconfigurations.
System Checks:
- GDM does not have TCP disabled
- Located in
/etc/gdm3/custom.conf - Set
DisallowTCPtotrue
- Located in
- GDM has xdmcp enabled
- Located in
/etc/gdm3/custom.conf - Set
Enabletofalseunder[xdmcp]
- Located in
- ECryptFS must be enabled for
testuser- Can be enabled via
ecryptfs-migrate-home - Can also be enabled via
ecryptfs-setup-private - Outlined in the readme
- Can be enabled via
- Firewall must be configured properly for the critical services
- Must be enabled via
sudo ufw enable - Log level must be configured
- Many ports must be open and configured
- Port 25 (SMTP) TCP
- Port 2049 (NFS) TCP
- Port 22 (SSH) TCP
- Port 110 (POP3) TCP
- Port 995 (POP3S) TCP
- Port 143 (IMAP) TCP
- Port 993 (IMAPS) TCP
- Must be enabled via
- Suderos group does not have a
syslogconfigured- Located in
/etc/sudoers - Include
syslog=authprivin theDefaultsline
- Located in
- Secure redirects must be set to 0
- Located in
/etc/sysctl.conf - Set
net.ipv4.conf.all.secure_redirectsto0
- Located in
- Bogus error responses are not ignored
- Located in
/etc/sysctl.conf - Set
net.ipv4.icmp_ignore_bogus_error_responsesto1
- Located in
- There is a bad source pulling from the wrong repo
- Remove the bad source from
/etc/apt/sources.list.d/- This source is pulling from the kali released which will mess you up!
- Remove the bad source from
Policies
There are a lot less policy checks on this virtual machine compared to the first Ubuntu box, but they are not particularly difficult so long as you are well prepared for them. Many of the policies are easy to check for via the command line, but others require a look into the specific config files.
Policy Checks:
authfailis not configured forpam_faillock- Located in
/etc/pam.d/common-auth - Must be set to
authfail
- Located in
- A secure hashing algorithm is not used for
pam_unix- Located in
/etc/pam.d/common-password - Set
yescrypt(latest) orsha512(older) forpam_unix
- Located in
Services
Services on this machine must be audited to ensure they are running and updated to the proper versions as defined in the readme.
Service Checks:
- Kernel is not updated
- Update via
sudo apt update && sudo apt upgrade - Ensure you fixed the bad source before you do this!!!
- Update via
vsftpdservice is not critical- Stop the service and delete it from the machine
sshdservice is not running- Reinstall and start the service
- Thunderbird needs to be updated
- Update via
sudo apt update && sudo apt upgrade
- Update via
- Dovecot needs to be updated
- Update via
sudo apt update && sudo apt upgrade
- Update via
Unwanted Software & Malware
I’m bundling media/unwanted files in this category too since I’m too lazy to make a new one at this point. Nearly all of these need to be manually audited by scouring the file system for anything that looks out of place.
Checks:
- Delete Rick-Roll mp3 file
- Located at
/home/perry/Music/NeverGonnaGiveYouUp.mp3
- Located at
- Remove
remmina(RDP client)- Located at
/usr/bin/remmina
- Located at
- Remove postfix reverse shell
- Located at
/usr/bin/postfix
- Located at
- Remove
strace- Located at
/usr/bin/strace
- Located at
- Remove
Autopsy- This check may be a little confusing since it’s ‘authorized’ on the Windows Server 2
- Located at
/usr/bin/autopsy
os-probercontains passwords for user accounts- Remove the passwords from the file
- Located in
/var/lib/os-prober
- Malicious python file located within
seddocumentation directory- Delete the file located at
/usr/share/doc/sed/sed/sed.py
- Delete the file located at
- Remove
enum4linux- Located at
/usr/bin/enum4linux
- Located at
Overview
I am sure that we missed a lot even in our retrospective, but I think we got a good amount of them. Feel free to leave a comment with any additional checks you found and I missed.
Fedora
Not much I can really say about this since we had virtually 0 time to work on the box due to issues outlined in the frustrations section.
Overall though, it was a really interesting virtual machine! The best part of it is definitely the fake terminal and bashrc malware. I really enjoyed that part.
Conclusion
While I am frustrated with many aspects of the competition and the ‘support’ given during it, I had a lot of fun practicing with my team. It is unfortunate that this was my last time competing, but I am glad I got to do it with my friends. I think it would be interesting to create a competition similar to this and create my own checks, so I may end up doing that at some point. I think a lot of the checks are honestly pretty dumb, and this year was a LOT harder than last year, but I still had fun preparing for it.
Thanks for reading!
Very Nice!